To this day, the main cybersecurity device used is PUF (Physical Unclonable Function), a physical object such as a chip or integrated circuit that detects device-specific differences in electronic properties. Although these act as a safe option to protect data, they present a main disadvantage: the difficulty to evaluate the uniqueness and ensure good reliability, making them sensible to modeling and physical attacks.
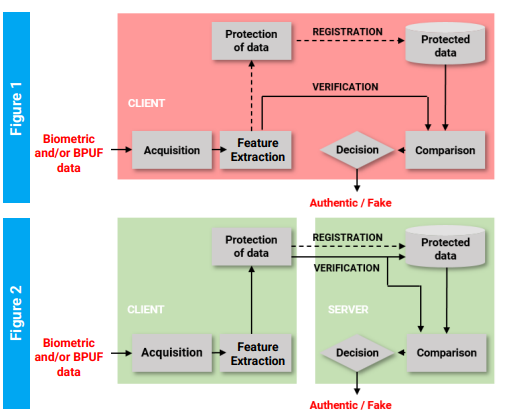
Additionally, among the current cryptographic trends, fuzzy extractors lead the list. These are authentication systems that employ a device-centric topology (Fig. 1), in which the acquisition of the PIN or biometric data, the processing, and the storage of the biometric templates are performed locally on the device with which it is accessed, for example, a smartphone. This poses a clear risk to device security, especially with the developments of very efficient and dangerous quantic computers.
Researchers from Universidad de Sevilla have developed a cybersecurity device that acts as a PUF but adds the advantageous characteristic that the detected properties are not only physical but also behavioral (BPUF), increasing the reliability and uniqueness of devices. Additionally, they propose a decentralized cryptographic method (Fig. 2) using BPUF, making transactions between servers and clients more cyber-safe.
The cryptographic methods for the protection and matching of protected information were successfully verified by considering code-based cryptography, facial biometrics, and the implementation in a smartphone.
The BPUFS have been analyzed experimentally using SRAMs of 90-nm CMOS technology and SRAMs in microcontrollers and Ring Oscillators in FPGAs of 90 nm and 28 nm.
Benefits:
- The cryptographic methods offer post-quantum security and satisfy irreversibility, privacy, revocability, and unlinkability properties.
- They are based on proven post-quantum algorithms.
- The client can perform secure electronic transactions, without storing cryptographic keys.
- The external evidence (proofs) can be employed for legal or forensics purposes.
- Security is achieved at a software and physical level.
- The risk of modeling and physical attacks to PUFs is reduced.
The represented institution is looking for a collaboration that leads to the commercial exploitation of the presented invention.
Institution: Universidad de Sevilla – Instituto de Microelectrónica de Sevilla (IMSE-CNM – Seville Institute of Microelectronics) and CSIC.
TRL: 5
Protection status: EU Patent Application.
Contact: Nuria Bas / nuria@viromii.com